How can cryptocurrency make the internet a more inclusive, liberated space?
Today’s internet is one of online censorship and surveillance. Maybe cryptocurrency can fix that.
Today’s internet is one of online censorship and surveillance. Maybe cryptocurrency can fix that.
Those of us who live in countries that have unrestricted, uncensored access to the internet can consider ourselves lucky (approximately 24% of the world’s population). We access the information or news sites that we please. We speak to and work with whomever we wish. While not perfect, the internet is at least a tool for us to learn, to communicate, to collaborate. We’re free use the internet as we see fit.
But that’s reality for just 24% of us.
For the other 76%, the internet is a place of unrealized possibilities. Government firewalls in restrictive countries censor their citizens to disallow access to information. To protect their interests, push a narrative for state-based media, control the knowledge of the populace, or restrict communication, they block websites that they deem unacceptable. Much of the world can’t access Facebook or Wikipedia, let alone a news site that presents unbiased information. In nations that heavily censor and restrict online interactions, expressing an idea on the internet can get you incarcerated. Or killed. It all depends on where you live.
However, no matter where you live, your ISP harvests and sells all your personal data to the highest bidder. While a more benign threat than government firewall censorship, this is still an invasive intrusion into the lives of ordinary internet users Accessing the internet shouldn’t mean that you have to allow another entity to gather all of your personal information and sell it to whomever they please.
We (the lucky 24%) are mostly unaware of these realities, especially state-sponsored censorship. But most of us would agree that the brightest minds in the world should have access to uncensored information and be able to communicate with their peers to further their research and foment new ideas. Most of us would also agree that regardless of nationality or geographic location, the citizens of the world have a right to speak to each other and access information without giving up all their personal information.
The question is, how do we change the the internet as it exists today into a network that is inclusive and censorship- and surveillance-free? How do we fight against increasingly centralized control over a tool that was created specifically to further diverse and open collaboration and community? Technologists have been asking these questions—and attempting to answer them—for the last couple of decades. So far, no one has been able to truly create a system that opens the internet to everyone. But blockchains and cryptocurrencies are facilitating new possibilities to create an internet that’s owned by no one and open to everyone.
There are several projects and teams attempting to tackle this complicated problem. At Orchid Labs, we think the best approach to solving the issues of censorship and surveillance is a decentralized, open-source, community-based protocol that incentivizes users in a peer-to-peer bandwidth exchange to allow anyone on Earth to access the internet as they see fit. The Orchid Protocol builds on the work that other internet-freedom advocates have proposed as solutions, while taking a new approach to the issues we all believe can and should be solved.
There have been multiple attempts to create a more open, secure internet. To date, the two most noteworthy technologies that allow users to access the internet without being monitored or censored have been virtual private networks (VPNs) and Tor. Both have had success and contributed to the movement of internet freedom, but both also come with limitations or drawbacks.
VPNs are widely used in the corporate world and by governments to access internal servers and transmit information securely. They’re also used by ordinary internet users around the world attempting to circumvent government firewalls and monitoring. In China alone, millions of people use VPNs to access parts of the internet that the Great Firewall blocks. Over the last year, the Chinese government has begun to crack down on VPNs, making unrestricted access more difficult for Chinese internet users.
VPNs use encryption to securely transport a VPN subscriber’s traffic across a larger insecure network. Once the VPN has received the traffic, it’s decrypted and re-transmitted across a separate large insecure network. The retransmission can assist users in circumventing access restrictions imposed by websites: internet traffic from a phone in China destined for Facebook’s servers will be identified and blocked, but traffic from that same phone to a non-descript VPN server (and then onward to facebook) may make it through. To a lesser extent, retransmission can reduce government or corporate tracking of website browsing habits. Encryption prevents the user’s ISP from seeing their traffic, thereby preventing monitoring attacks. The VPN provider, however, can still decrypt the traffic even if your ISP cannot. Any attack an ISP could previously perform can easily be performed by the VPN. All that changes is who you choose to trust with your privacy.
VPNs are a centralized solution. Although VPN service providers face more competition than ISPs, they ultimately draw talent from the same sources, and have similar bandwidth-for-cash-type subscription business models. Because of that, users can’t simply assume their VPN provider is trustworthy. It’s likely that VPN providers will eventually fall prey to the same incentives that led the user to not trust their ISP.
Additionally, the re-use of IP addresses for relaying traffic in VPN setups enables relative ease in blocking their use by commercial websites. While VPNs relay traffic through multiple servers, state actors wishing to censor the internet have recently been cracking down on them by attacking the servers and significantly inhibiting and disrupting the service that they provide.
Tor is a free software project that enables anonymous communication. It’s famous for introducing the idea of “onion routing” to a wider audience. Tor is a global, decentralized system with several participants who run computers or “nodes” across the Internet. Participants download a global list of nodes, randomly select from that list, and form onion routes from their selection. Onion routes are an ordered list of nodes. Packets of internet data are sent along a route that includes several nodes between you and the website you want to visit. Onion routing means that the packets are encrypted for each node in turn (so like an onion, the encryption has several layers) and such that each participant will only know where to send the packet next, not the full route of the packet from you to a website. Unless several computers in between are compromised or run by the same participant, no two participants know both who sent a packet and where it went.
Tor’s success has been limited both by a lack of widespread adoption and by mainstream association with the dark web. It’s supported by roughly seven thousand unpaid volunteers, the node-running participants we described earlier.. That’s not very many nodes, meaning that sophisticated attackers have a tractable number of nodes to monitor or otherwise compromise.
Both VPNs and Tor have significantly influenced technologists attempting to create a more secure, open internet. And while both approaches have tried to create an internet experience free of censorship, neither has fully succeeded. Regardless, the shared experience of both—in their successes and failures—are something that we can learn from, build on, and utilize to attempt to create a system that is more widely adopted and more secure.
By learning from the efforts of those in the past, we believe that we’ve created a protocol that can finally solve the problems of censorship and surveillance. The Orchid Protocol, the first application available on the Orchid Network, is an open-source overlay network that runs on top of the internet. It is fully decentralized, because rather than traffic being routed through central authorities—your ISP or your VPN—it’s instead routed randomly through a network of bandwidth contributors who sign up to share their surplus bandwidth and activate their internet-connected device as a node.
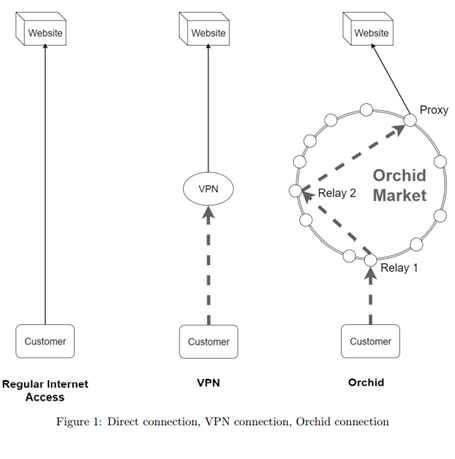
Unlike previous efforts that relied on volunteer nodes, like Tor, the Orchid Network is a market-based, fully decentralized, and anonymous peer-to-peer system based on “bandwidth mining,” which we believe addresses the lack of relay and exit nodes by directly incentivizing participants. Like many online features that users pay for but don’t consume all of or fully utilize (bandwidth, cloud-based storage, edge services, etc.), unused bandwidth is a wasted resource. The Orchid Network gives you an opportunity to share that unused bandwidth, which would otherwise go unused and vanish, and receive a tokenized payment in return. Users that want to access an uncensored internet (bandwidth consumers) pay the bandwidth contributors in Orchid tokens (an Ethereum-based ERC20 token), through a peer-to-peer exchange. Because this utilizes the Ethereum blockchain, neither the traffic nor the payments can be monitored by central authorities, and both contributors and consumers of bandwidth enjoy a fully anonymous, surveillance-free experience.
Orchid relays and proxies can be viewed as just-in-time purchased VPNs chained together. Unlike traditional VPNs, Orchid proxies and relays don’t know the identity of their customers, nor do they know the IP address their customers are using. By addressing the limitations of VPNs and Tor with new architecture that relies on distributed networks with users who are incentivized to share bandwidth via tokenized micropayments, we believe that the Orchid protocol will be utilized and adopted on a scale that is capable of defending attacks.
Blockchains are, in their most basic definition, open-source protocols designed to store authenticated transaction information, utilize peer-to-peer interactions, and they can be downloaded and used for free, thus eliminating intermediaries (state-based or corporate). The transactions occur without either party or a central authority knowing the identity of the parties engaged in the transactions.
Blockchain protocols run on computers on the internet, commonly referred to as nodes. These nodes eliminate central points of attack, which stabilizes and secures the network against attacks. While some large financial institutions and government entities are starting to implement blockchains for their own purposes, the original blockchains—and most of those that exist today—use cryptocurrencies to incentive the nodes to participate and further secure the network. Of the various cryptocurrency incentivized blockchains in existence today, the one most commonly known by the public is the Bitcoin network.
Bitcoin revolutionized the status quo of traditional payment systems and continues to disrupt global markets for payments and international transfers. It utilizes a global network and protocol unaware of geographical boundaries. Applying public-key cryptography, transactions transfer Bitcoin amounts between addresses generated by the users themselves, without the need for any trusted party. Users generate key pairs, where a hash of the public key can be used as a payment address, requiring the private key to sign transfers from the address.
Completed Bitcoin payments are unforgeable and irreversible. Bitcoin payments are pseudo-anonymous and the level of anonymity depends to a large extent on how the network is used.
In general, decentralized cryptocurrencies allow humans and computer systems alike, for the first time in history, to transact value without trusted third parties—a crucial requirement for incentivized, distributed overlay networks such as Orchid. At present, however, Bitcoin transaction fees are high; average fees have been as high as $8, rendering applications relying on low fees, as Orchid would, infeasible on the Bitcoin network.
The Ethereum network, also rooted in public-key cryptography and secured by proof-of-work like Bitcoin, derives the same properties of unforgeability, availability, and irreversibility. Ethereum has a higher and dynamically adjustable transaction capacity; the network has seen low fees since its launch in 2015.
However, due to an increased number of transactions as well as price growth of Ethereum’s underlying native token, Ether, transaction fees (known as gas) have grown to an average of $0.20 with peaks up to $1.00. Transactions executing smart contract code cost even more, in proportion to how much computation is performed. The increase in transaction fees in popular, public blockchain networks inhibit their potential for handling micropayments directly, pushing micropayments to second-layer solutions such as payment channels.
An Orchid node may service thousands of other nodes and users may use hundreds of nodes to access different websites. Thus, the transaction fees of setting up a payment channel between each node (even if using networks of channels such as the Raiden Network) would be prohibitive.
In order to solve this issue, we use probabilistic micropayments on Ethereum, another technology that’s only been made possible because of decentralized cryptocurrencies and the smart contracts they enable.
Probabilistic micropayments allow people to pay only for what they use, rather than purchasing a subscription for a service, which the user may or may not use often enough to justify the cost. By building a platform where you can pay for only what you use in amounts down to fractions of pennies, we’re creating a mechanism that puts more power in the hands of users, rather than corporations or governments.
At Orchid Labs, our protocol software is 100% open source, because we believe that a decentralized solution is the only way to achieve our common goals. By building on the contributions of other technologists attempting to solve issues related to a more open, inclusive, and secure internet, we’ve created a protocol that can help internet users around the world enjoy a censorship- and surveillance-free experience. By using a system where bandwidth contributors and bandwidth users exchange resources via probabilistic micropayments for what they require and nothing more, we’ve created a platform that gives internet users more power and more possibilities.
To find out more—including a whitepaper describing the technology—visit www.orchidprotocol.com.
Stephen Bell is the Co-Founder of Orchid Labs.