Public blockchain cryptocurrencies such as Bitcoin are radically transparent at the protocol level: transactions are viewable and immutable to everyone forever on the blockchain ledger. They are not anonymous, but rather are pseudonymous, like email addresses. And just as a person can opt to use extra privacy-preserving techniques for email, cryptocurrency users can adopt special cryptographic technologies to secure more privacy for themselves.
This explainer will describe a few of the most popular privacy-preserving techniques in the cryptocurrency space and will explain how they work. As we will see, there are multiple ways to achieve extra privacy with cryptocurrency transactions, and many reasons why users might want to adopt these methods.
The computing challenge, in a nutshell
Bitcoin and similar cryptocurrency transactions are made up of one or more specified currency amount inputs (to the recipient) and one or more specified currency amount outputs (from the sender) at a certain time, all of which are recorded on the blockchain as what is called an “unspent transaction output” (UTXO). Each input was at one point the output of a previous transaction. The aggregated linkages of inputs and outputs can be traced using blockchain analysis programs.
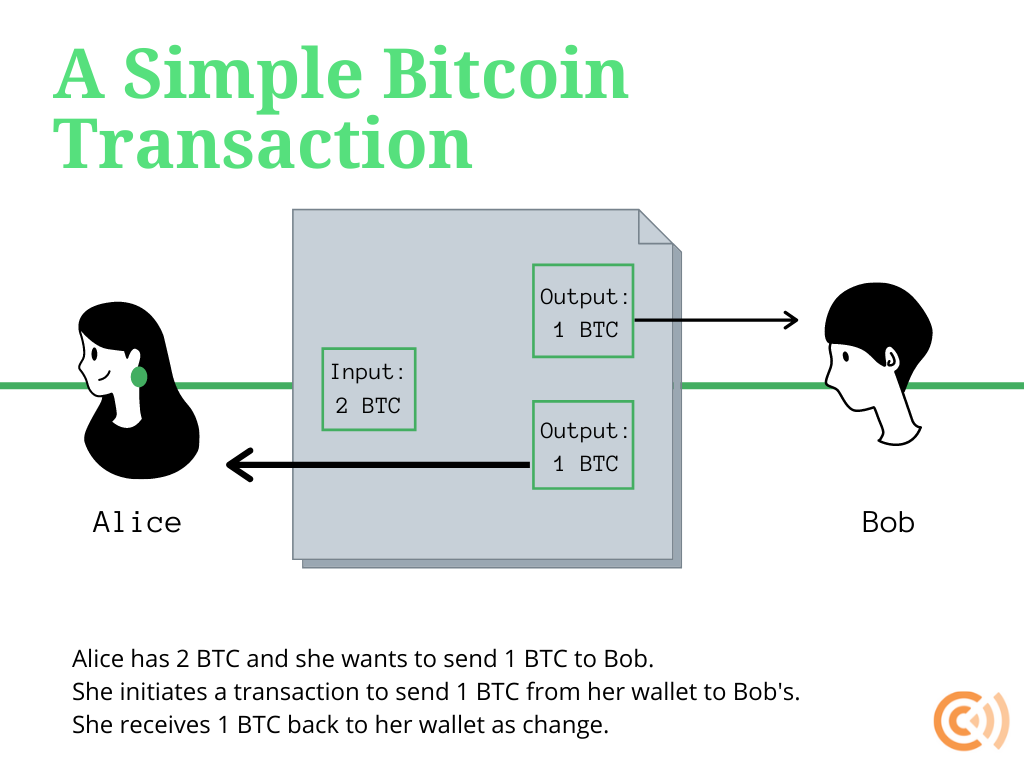
Although users can create as many addresses to send or receive transactions as they would like, if they are not careful, they can easily leak data to uninvolved parties. Depending on how the transaction is structured, through blockchain forensics it may be possible to unmask the identity of the sender, recipient, or both, along with the amount of money sent.
For example, let’s say that a user displays a public address on his personal webpage to solicit cryptocurrency donations from supporters. He lives under a repressive government that does not grant freedom of the press. If that user sends cryptocurrency from his identity-linked address to a newly-created address to purchase a censored newspaper subscription, the government could trace that transaction back to his identity-linked address and punish him.
Here is another example. Let’s say that a non-governmental organization exists to help people living under repressive regimes. The NGO uses cryptocurrency to help fund dissidents in their activities. A repressive government can look at the transactions emanating from the NGO’s address to hunt down activists.
Individuals who wish to maintain privacy should not structure their transactions as described above. They can employ one of many privacy-preserving techniques for cryptocurrency transactions that have been developed to shield the sender, recipient, or amounts involved, or some combination of these, from unrelated observers. This can be done through mixers, CoinJoins, or protocol-level features of certain privacy-preserving cryptocurrencies.
Mixers and CoinJoins
There are two broad techniques to attain more privacy with Bitcoin transactions. A user can seek out a “mixer” service, which is generally offered by a third-party custodian, or undertake a “CoinJoin” transaction, which is always non-custodial.
Mixers, also known as “tumblers,” were one early Bitcoin privacy technique. The process is straightforward: privacy-seeking cryptocurrency users would send transactions to a mixer service which, in exchange for a fee, would then “mix” the pool of cryptocurrency together to de-link the transaction trail.
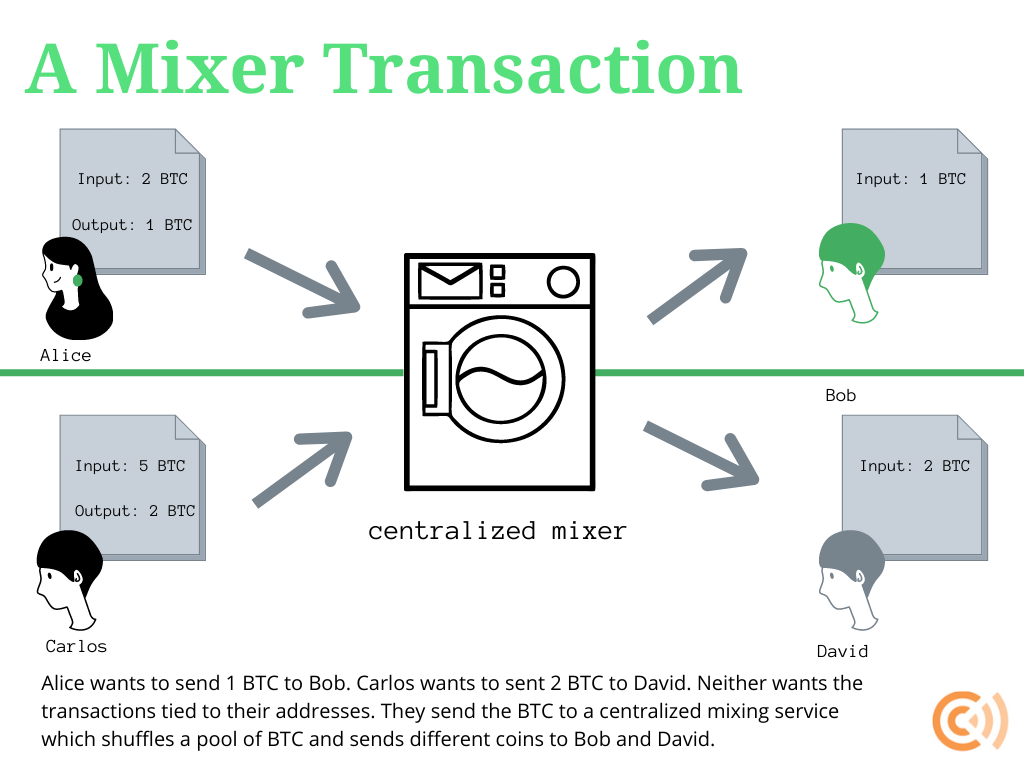
Initially, mixer services were only offered by third parties, which had to be trusted. This centralization means that mixer users are at the mercy of service providers. A dishonest mixer could secretly keep records of transactions or poorly mix the coins. In the extreme case, a mixer could simply abscond with the money.
But simple centralized mixing has a huge downside even when mixers are perfectly honest and capable: non-criminal mixer users may receive coins that are tainted by criminals that use that same mixing service. In other words, although privacy may be more preserved with a simple centralized mixer, a non-criminal user may still receive coins with a “taint” of someone else’s crime. Because receiving tainted coins is undesirable, this creates a problem of imperfect fungibility since untainted coins may be worth more than tainted coins.
Improvements to this model were eventually made. For example, a “smart pool” mixer combines user-submitted funds, which might include the proceeds of a criminal act, with private reserves from the mixer and investors, which are unlikely to have been associated with any crime. A “stealth pool” takes this logic even further, completely separating user-submitted coins from reserve and investor coins that are paid out to new addresses; in other words, there is little chance that a user will receive tainted coins. Mixing services may also delay payments over a set period of time or spread out payments among separate wallets to further obfuscate the trail.
Eventually, more peer-to-peer methods to preserve privacy were developed. These achieve a similar end to centralized mixing—namely, concealing transaction senders, recipients, or amounts or some combination of these—with fewer of the downsides.
Bitcoin developers had been working on a non-custodial transaction privacy tool called CoinJoin since 2013. With a CoinJoin transaction, two or more senders combine their inputs to be sent to two or more output recipients. The inputs sum to the amount of the outputs, yet an observer looking at the blockchain would not be able to easily tell any address, sender identity, or sum involved. Even the recipient of a CoinJoin transaction could not tell the sender’s address just looking at the blockchain. Recipient addresses, however, would be viewable on the blockchain.
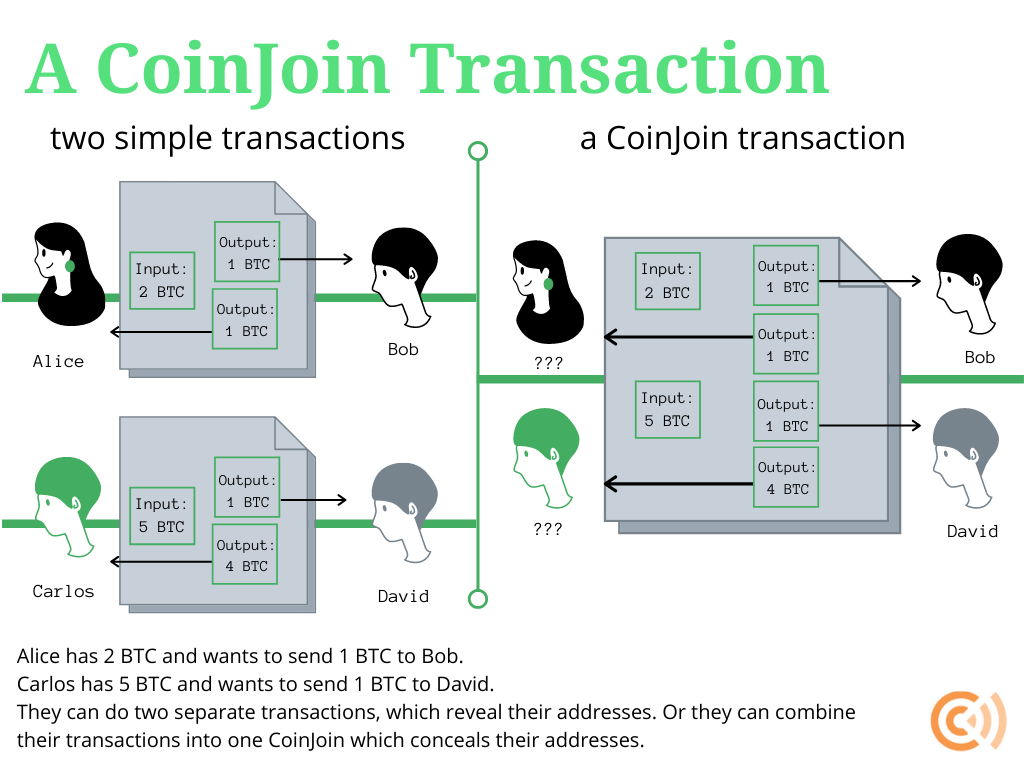
Today, CoinJoin functionality is offered by popular wallet software. CoinJoin transactions were first offered by the Dark Wallet alpha release in 2014. Today, wallets like Wasabi and Samourai offer CoinJoin options to users. Importantly, CoinJoins operate on a non-custodial basis. It is simply a Bitcoin transaction type that individual users can initiate, not a service that requires a third party to control keys or coins.
One limitation of CoinJoin transactions is that they require users to coordinate to send the transaction at the same time. Wallet software provided by Wasabi and Samourai—particularly Samourai’s recent Whirlpool application—helps to alleviate this problem somewhat by making it easier for users to initiate CoinJoins, but users may still have to wait to find others to join in the transaction. Although Wasabi and Samourai software makes it easier for their users to initiate CoinJoins, neither service provider acts as a custodian. At no point do Wasabi and Samourai wallet developers have control of user keys.
A special CoinJoin application called JoinMarket overcomes this problem by allowing users to pre-pay for a CoinJoin. Users who don’t mind waiting to make a transaction, called market-makers, collect fees from users who would like to quickly make a payment, called market-takers. At no point does any party have complete control over transaction funds—JoinMarkets are non-custodial.
A developing variant of a CoinJoin, called a CoinSwap, may overcome the limitations of recipient vulnerability and equal-input requirements. In a CoinSwap, users send coins to a multi-signature address—or a wallet that requires signatures from some majority of n private keys in order to move funds—that are withdrawn on the other side from the wallets of the other users. A special cryptographic trick called a hash-time-locked contract prevents any party from stealing funds. The key benefit of a CoinSwap is that the transaction looks like a simple transaction on the blockchain, when in reality, the parties to a CoinSwap concealed the senders and recipients addresses from the blockchain. Privacy-preserving wallet services like Wasabi are already examining how they can integrate CoinSwap functionality in their software.
Privacy-preserving cryptocurrencies
The optional privacy-preserving Bitcoin tools described above improve on the general lack of privacy with simple Bitcoin transactions. However, they may still leave some kind of trace, limited though it may be, on the blockchain if they are not perfectly executed. They are also complex and sometimes cumbersome to use, so less technical users may find it difficult to adequately wield them.
Furthermore, since these tools are not the default mode of interacting with the bitcoin blockchain, some worry that using them may draw unwarranted attention from third parties and law enforcement. For example, third party exchanges may block or track transactions that they believe have come from a privacy technique like a CoinJoin transaction. This would be a problem from Bitcoin fungibility, since certain coins would be less marketable than others. Additionally, without privacy by default, innocent non-technical users who are unfamiliar with their options may be denied privacy protections that should, arguably, automatically protect all.
For these reasons, some developers have endeavored to create cryptocurrencies that implement privacy techniques at the protocol level. These “privacy-preserving cryptocurrencies,” or “privacycoins,” are separate from Bitcoin. They are peer-to-peer blockchain-based cryptocurrencies, but they operate in special ways to conceal senders, recipients, or amounts, or some combination thereof, from third parties.
One of the reasons that cryptocurrencies like Bitcoin are radically transparent is that it allows anyone to view the blockchain and verify that transactions are accurate. In other words, there is a tradeoff between privacy and authentication. Custom built privacy-preserving cryptocurrencies endeavor to build a technological way to provide both privacy and authentication.
One of the oldest privacy-preserving cryptocurrencies is Zcash, born in 2016 from earlier academic research projects, Zerocoin and Zerocash. Like Bitcoin, Zcash is peer-to-peer cryptocurrency with a supply limit of 21 million that is maintained and validated by an open network of miners. But Zcash can afford greater privacy at the protocol level through the application of what are called zk-SNARKs, or “zero-knowledge Succinct Non-Interactive arguments of Knowledge.” In a nutshell, Zcash gives users the default option to transact using a public address, just like a Bitcoin address, or a private “shielded” address, which is hidden yet verifiable on the blockchain using zk-SNARKs.
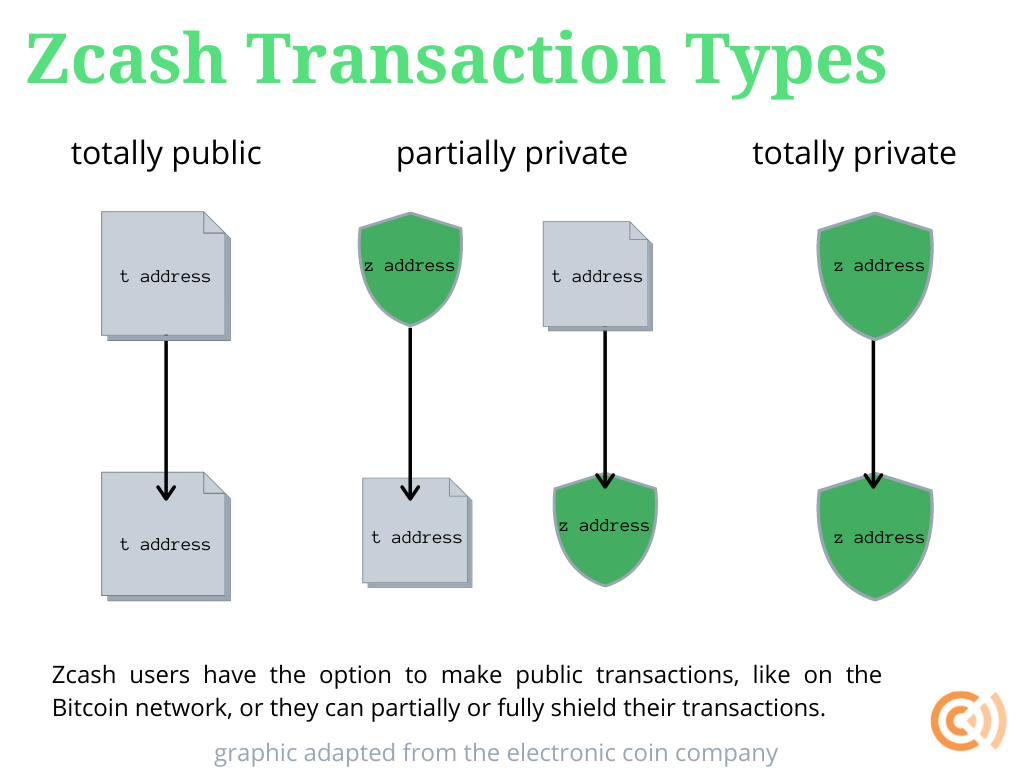
A zero-knowledge proof is a mathematical technique for one party to prove to another that a statement is true without revealing anything other than the validity of the statement itself. When applied to Zcash, the proof in question is that a given transaction is valid.
Zcash’s bleeding-edge use of zk-SNARKs has been characterized as “so mind-bending it seems taken from the pages of a science fiction novel.” Although uniquely innovative and developed by well-known cryptographers, shielded transactions still constitute a minority of all Zcash activity compared with fully transparent transactions: as of May of 2020, only 6 percent of Zcash transactions were fully shielded (meaning a shielded address sent money to another shielded address) while 15 percent were partially shielded (meaning a transparent address sent money to a shielded address or vice versa).
Shielded transactions can also be accompanied by an encrypted memo field to convey transaction details—otherwise kept private—to relevant parties; shielded transaction details can also be made visible to third parties or the public at large by sharing a “view key” that’s otherwise kept private by senders and recipients. Though novel and complicated, Zcash provides one compelling option for cryptocurrency users seeking enhanced privacy.
Another popular privacy-preserving cryptocurrency is called Monero, from the Esperanto word for money. With Monero, all senders, recipients, and amounts are concealed by default, but users have the option to share certain information with intended recipients if they desire. This is why the Monero project describes itself as “private by default and optionally semi-transparent.”
Monero preserves the privacy of senders through what is called a ring signature. When a Monero user broadcasts a transaction, their personal signature is combined into a group of other Monero users’ signatures so that an observer cannot tell which signature actually produced the initiating signature. Every Monero transaction is structured this way by default, so no user draws attention to themselves by choosing whether or not to use ring signatures.
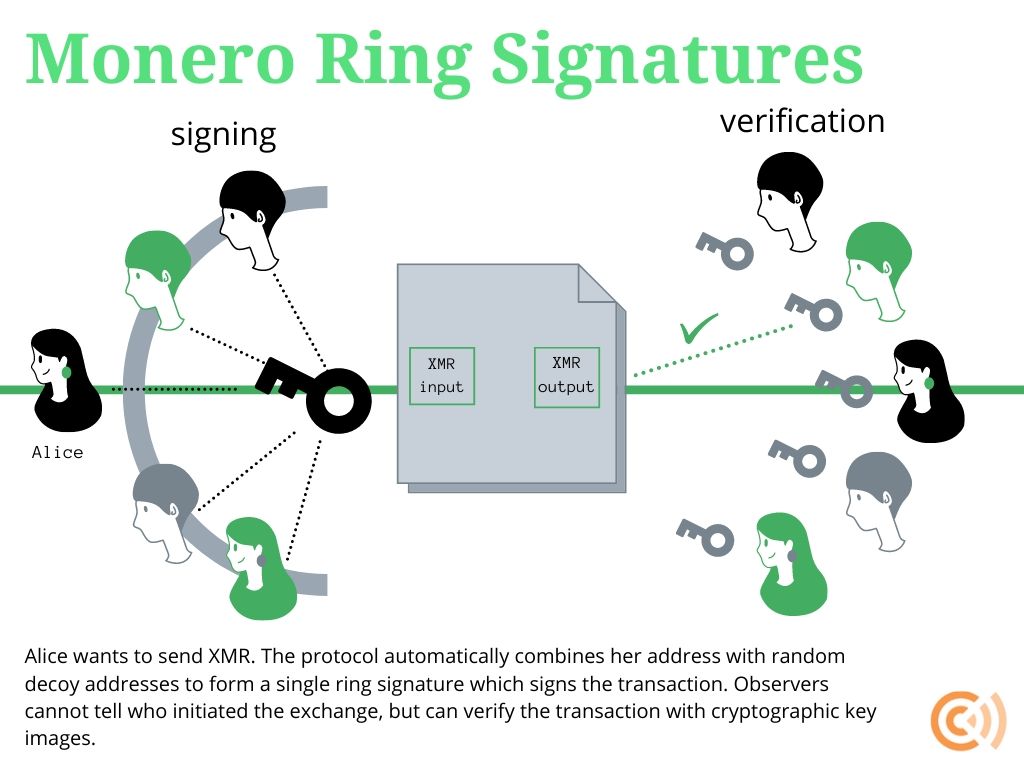
A special kind of ring signature, called ring confidential transactions or RingCT, conceals transaction amounts in Monero. RingCT was implemented in January 2017 and is now mandatory for all network transactions. Just like ring signatures and zero-knowledge proofs, the “multi-layered linkable spontaneous anonymous group signature” or MLSAG at the core of RingCT conceals private data while allowing observers to verify that transactions are authentic with special encryption techniques. RingCTs are also non-custodial and do not require full third-party control of coins.
A final default privacy tool on Monero is called a stealth address, which conceals recipients. Each user has a public address that is 95 characters and starts with a 4. But whenever someone sends money to a public address, it is actually sent to an auto-generated stealth address that no unrelated observer can see. Monero users have the option to reveal their transactions and account balances if they would like if they choose to reveal their private view key. But Monero transactions are structured to be automatically private by default.
As with Bitcoin and Zcash, Monero presents certain weaknesses. For instance, questions surround Monero’s auditability. Bitcoin’s radical transparency presents challenges for privacy, but it makes technologically auditing individual entities and the total currency supply trivially easy. Monero’s default privacy makes such auditing more difficult; for example, an undiscovered bug could inflate the Monero money supply in a way that is hard to detect. (Still, inflation bugs have also occurred with public blockchain cryptocurrencies like Bitcoin and hybrid cryptocurrencies like Zcash.) Monero developers acknowledge this limitation and urge users to evaluate their own risk preferences involved with the privacy/auditability tradeoff. (Shielded Zcash transactions present a similar auditability problem.)
Zcash and Monero are just two privacy-preserving cryptocurrencies. We have highlighted these two to contrast two different approaches and describe some of the tools they use. Other examples include Mimblewimble implementations like Grin and Beam (which use confidential transactions techniques) and Komodo (which is a fork of Zcash).
Use cases and implications
It is true that privacy-preserving technologies and cryptocurrencies may be used for unwanted activities, just as it is true that cash may be used in such ways. But there are many socially beneficial uses of privacy-preserving technologies and cryptocurrencies that far outweigh the minority of undesired uses. Besides, the right to privacy is a core component of living in an open society.
For example, privacy-preservation techniques improve individual security. Let’s say a business accepts cryptocurrency and amasses a small fortune in their public address. A criminal viewing the blockchain could find that business to be an irresistible target. She could break into the business, hold a gun to someone’s head, and demand the private keys to steal the money. Using privacy technologies can make a business less vulnerable to such attacks.
Or consider someone who does not wish to have their behavior scrutinized and influenced, like through advertisements targeted based on previous purchases. If a person’s wallet is linked to their identity, marketing agencies can analyze their transactions to try to track them across the web and sell them goods and services. Using privacy techniques shields users from ad tracking.
There are more prosaic applications of privacy technology. Let’s say someone wants to get their tech-savvy spouse a surprise gift for their birthday without it being tracked on their shared accounts. A sneaky wife may check her husband’s cryptocurrency wallet to try to get an idea of her gift. Privacy tools help preserve the joy of a holiday secret.
More fundamentally, the right to privacy is a foundational part of the open society. Free peoples may decide what to share or conceal from the public. It is a human right, and it is one that is now available with digital purchases thanks to privacy-preserving cryptocurrency tools. A globally accessible list of all citizen’s transactions may be a boon to law enforcement but it is also a disaster for pro-democracy agitants living under oppressive totalitarian regimes.
Fortunately for policymakers, the legal implications of these technologies are similarly clear. Privacy techniques that involve third party control of funds and keys, such as centralized mixer services, are subject to surveillance regulations intended for custodial services. Techniques and cryptocurrencies that do not involve third party control of funds and keys, such as CoinJoins, Zcash, and Monero, are not subject to such regulations but, again, custodial entities within those ecosystems, e.g. an exchange that sells consumers a privacy protecting cryptocurrency, are.
The Financial Crimes Enforcement Network of the US Treasury Department (FinCEN), the top federal money-laundering watchdog organization in the US, has issued clear rules on which cryptocurrency entities are subject to financial regulations that distinguish custodial from non-custodial applications, exempting the latter. Specifically, mere users, software developers, miners, and multi-signature wallet transactions involved with privacy-preserving cryptocurrency techniques are non-custodial and therefore exempt. Custodial parties, such as centralized mixers, are not exempt.
Andrea O’Sullivan is director of Technology and Innovation at the James Madison Institute and visiting fellow at Coin Center.
This post has been updated to correct errors in the original draft. Thanks to @maxtannahill and @DiverterNoKYC for the feedback.